SAML Concepts: Difference between revisions
No edit summary |
|||
| Line 34: | Line 34: | ||
Single sign-on (SSO) is not strictly a SAML concept. However, because SAML provides a trusted way to share security information, applications using SAML can participate in single sign-on scenario where the identity of a subject is verified by a party and other party uses it because it trusts the first party and the communication mechanisms between them. SAML requires the user to enroll with at least one SAML-enabled security provider. The identity of the user will be verified (authenticated) by that security provider. [[#Web_Browser_Single_Sign-On|Web browser single sign-on]] is a SAML profile. | Single sign-on (SSO) is not strictly a SAML concept. However, because SAML provides a trusted way to share security information, applications using SAML can participate in single sign-on scenario where the identity of a subject is verified by a party and other party uses it because it trusts the first party and the communication mechanisms between them. SAML requires the user to enroll with at least one SAML-enabled security provider. The identity of the user will be verified (authenticated) by that security provider. [[#Web_Browser_Single_Sign-On|Web browser single sign-on]] is a SAML profile. | ||
=SAML Profile= | =SAML Profile= | ||
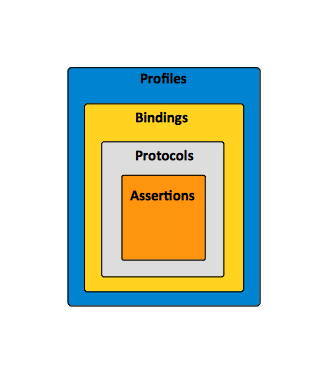
A ''profile'' is essentially a use case for SAML. A profile combines [[#SAML_Assertion|assertions]], [[#SAML_Protocol|protocols]] and [[#SAML_Binding|bindings]] to support specific use cases. For example, the Web Browser SSO Profile specifies how SAML authentication assertions are communicated between an [[#Identity_Provider|Identity Provider]] and [[#Service_Provider|Service Provider]] to enable single sign-on for a browser user. | A ''profile'' is essentially a use case for SAML. A profile combines [[#SAML_Assertion|assertions]], [[#SAML_Protocol|protocols]] and [[#SAML_Binding|bindings]] to support specific use cases. For example, the Web Browser SSO Profile specifies how SAML authentication assertions are communicated between an [[#Identity_Provider|Identity Provider]] and [[#Service_Provider|Service Provider]] to enable single sign-on for a browser user. From a high level perspective, several notable SAML use cases are Web Browser Single Sign-On, Attribute-based Authorization, Identity Federation and WS-Security. | ||
[[Image:SAML_Concepts_Profile_Binding_Protocol_Assertion.png]] | [[Image:SAML_Concepts_Profile_Binding_Protocol_Assertion.png]] | ||
Revision as of 02:36, 21 February 2017
Internal
Security Assertion
Subject
Subjects are entities that have identity related information specific to a security domain.
Security Domain
Identity Provider
The Identity Provider (IdP) is.
The Identity Provider is also known as the asserting party.
Service Provider
The Service Provider (SP) is ....
The Service Provider is also known as the relying party.
Trust Relationship
There is a trust relationship between the Identity Provider and and the Service Provider.
Token
A SAML token is a type of token issued by a STS/IdP that can be used to enable SSO. A relying resource secured by SAML will redirect users to SAML identity provider to obtain a valid SAML token before authenticating and authorizing the user.
Single Sign-On (SSO)
Single sign-on (SSO) is not strictly a SAML concept. However, because SAML provides a trusted way to share security information, applications using SAML can participate in single sign-on scenario where the identity of a subject is verified by a party and other party uses it because it trusts the first party and the communication mechanisms between them. SAML requires the user to enroll with at least one SAML-enabled security provider. The identity of the user will be verified (authenticated) by that security provider. Web browser single sign-on is a SAML profile.
SAML Profile
A profile is essentially a use case for SAML. A profile combines assertions, protocols and bindings to support specific use cases. For example, the Web Browser SSO Profile specifies how SAML authentication assertions are communicated between an Identity Provider and Service Provider to enable single sign-on for a browser user. From a high level perspective, several notable SAML use cases are Web Browser Single Sign-On, Attribute-based Authorization, Identity Federation and WS-Security.
For more details on SAML profiles, see:
SAML Binding
SAML protocol bindings are the mappings from SAML request/response message exchanges into standard messaging or communication protocols. For more details see:
SAML Protocol
Requests and responses for obtaining assertions and doing identity management.
SAML Assertion
Authentication, attribute and entitlement information.
Authentication Context
Detailed data on types and strengths of Authentication.
Metadata
Configuration data for identity and service providers.
To Deplete
- https://home.feodorov.com:9443/wiki/Wiki.jsp?page=SingleSignOn
- https://home.feodorov.com:9443/wiki/Wiki.jsp?page=PicketLinkSAMLSSO#section-PicketLinkSAMLSSO-Concepts