SAML Architecture: Difference between revisions
| Line 8: | Line 8: | ||
[[File:SAML_Domain_Model.png]] | [[File:SAML_Domain_Model.png]] | ||
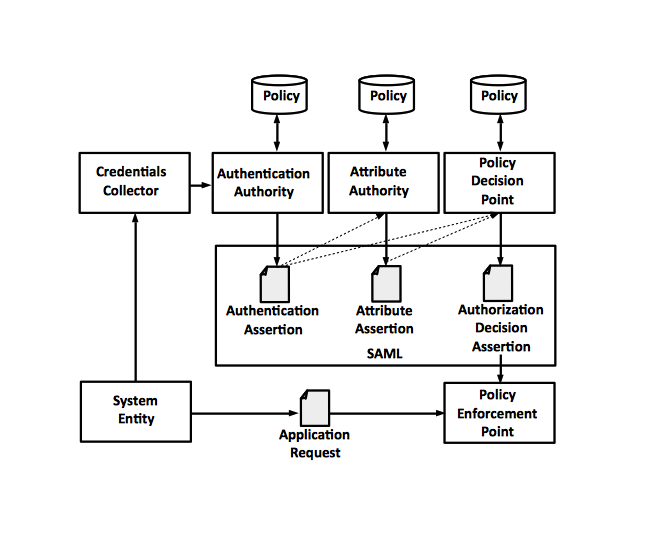
A system entity (client) wants to access a system resource. The system entity presents user credentials to the [[#Credential_Collector|Credential Collector]], which will authenticate with the associated [[#Authentication_Authority|Authentication Authority]], producing the [[SAML Concepts#Authentication_Assertion|authentication assertion]] | |||
==Credential Collector== | ==Credential Collector== | ||
Revision as of 06:34, 21 February 2017
Internal
Domain Model
SAML is specified by the following domain model:
A system entity (client) wants to access a system resource. The system entity presents user credentials to the Credential Collector, which will authenticate with the associated Authentication Authority, producing the authentication assertion
Credential Collector
A system object that collects user credentials to authenticate with the associated Authentication Authority, Attribute Authority, and Policy Decision Point.
Authentication Authority
A system entity that produces authentication assertions.
Session Authority
A system entity (for example, Identity Provider) that plays the role of maintaining the state related to the session. Also see single logout profile.
Atribute Authority
A system entity that produces attribute assertions.
Attribute Repository
A repository where attribute assertions are stored.
Policy Repository
A repository where policies are stored. Also known as "Policy".
Policy Decision Point
A system entity that makes authorization decisions for itself or for other system entities that request authorization.
Policy Enforcement Point
A system entity that enforces the security policy of granting or revoking the access of resources to the service requester.
Policy Administration Point
A system entity where policies (for example, access control rules about a resource) are defined and maintained.