SAML Architecture: Difference between revisions
| (4 intermediate revisions by the same user not shown) | |||
| Line 17: | Line 17: | ||
==Authentication Authority== | ==Authentication Authority== | ||
A system entity that produces [[SAML Concepts#Authentication_Assertion|authentication assertions]]. | A system entity that produces [[SAML Concepts#Authentication_Assertion|authentication assertions]]. Usually, the authentication authority is implemented by an authentication service. | ||
==Session Authority== | ==Session Authority== | ||
| Line 25: | Line 25: | ||
==Attribute Authority== | ==Attribute Authority== | ||
A system entity that produces attribute assertions. | A system entity that produces attribute assertions. Usually, the attribute authority is implemented by a directory server that stores policy attributes. | ||
==Attribute Repository== | ==Attribute Repository== | ||
| Line 37: | Line 37: | ||
==Policy Decision Point== | ==Policy Decision Point== | ||
A system entity that makes authorization decisions for itself or for other system entities that request authorization. | A system entity that makes authorization decisions for itself or for other system entities that request authorization. Usually, the policy decision point is implemented by a policy server that determines what the client is entitled to. | ||
==Policy Enforcement Point== | ==Policy Enforcement Point== | ||
| Line 45: | Line 45: | ||
==Policy Administration Point== | ==Policy Administration Point== | ||
A system entity where policies (for example, access control rules about a resource) are defined and maintained. | A system entity where policies (for example, access control rules about a resource) are defined and maintained. The policy information may include actions, conditions, or dependencies that are associated with the access of resources. They reside in a policy repository, which is usually implemented in a database or directory server. | ||
Latest revision as of 07:04, 21 February 2017
Internal
Domain Model
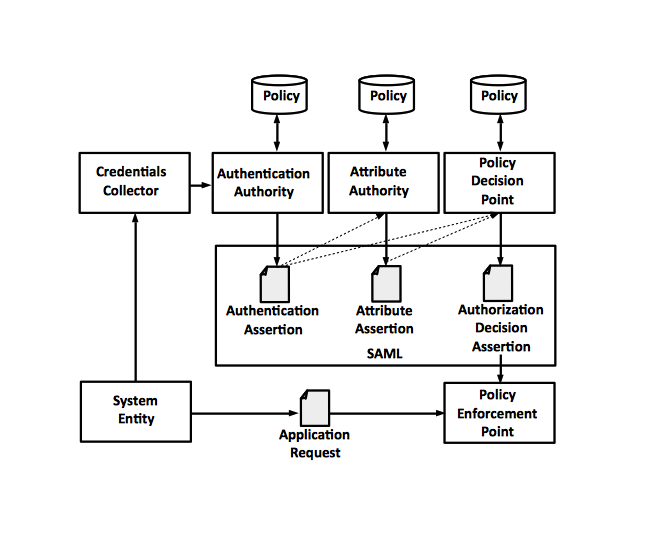
SAML is specified by the following domain model:
A system entity (client) wants to access a system resource. The system entity presents user credentials to the Credential Collector, which will authenticate with the associated Authentication Authority, producing the authentication assertion, then with the Attribute Authority producing an attribute assertion and the Policy Decision Point, producing the authorization decision assertion, before the system entity can be granted access. The Policy Enforcement Point will process the application request based on the access rights granted. All assertion requests are represented in SAML.
Credential Collector
A system object that collects user credentials to authenticate with the associated Authentication Authority, Attribute Authority, and Policy Decision Point.
Authentication Authority
A system entity that produces authentication assertions. Usually, the authentication authority is implemented by an authentication service.
Session Authority
A system entity (for example, Identity Provider) that plays the role of maintaining the state related to the session. Also see single logout profile.
Attribute Authority
A system entity that produces attribute assertions. Usually, the attribute authority is implemented by a directory server that stores policy attributes.
Attribute Repository
A repository where attribute assertions are stored.
Policy Repository
A repository where policies are stored. Also known as "Policy".
Policy Decision Point
A system entity that makes authorization decisions for itself or for other system entities that request authorization. Usually, the policy decision point is implemented by a policy server that determines what the client is entitled to.
Policy Enforcement Point
A system entity that enforces the security policy of granting or revoking the access of resources to the service requester.
Policy Administration Point
A system entity where policies (for example, access control rules about a resource) are defined and maintained. The policy information may include actions, conditions, or dependencies that are associated with the access of resources. They reside in a policy repository, which is usually implemented in a database or directory server.