OpenShift Security Concepts: Difference between revisions
| Line 51: | Line 51: | ||
==Service Account== | ==Service Account== | ||
A ''service account'' is a special, non-human [[#System_User|system user]] that acts automatically and requires access to objects in its own project or other projects. Service accounts are associated with projects (namespace-scoped) | A ''service account'' is a special, non-human [[#System_User|system user]] that acts automatically and requires access to objects in its own project or other projects. Service accounts are associated with projects (namespace-scoped). | ||
Service accounts are typically used by services such as routers and registries, or when system components need to make an API call to the master: for example, when replication controllers make API calls to create or delete pods, when [[Jenkins_and_OpenShift#Security_Considerations|Jenkins interacts with the master to start a build, or when an external application makes API calls for monitoring and integration purposes. | Service accounts are typically used by services such as routers and registries, or when system components need to make an API call to the master: for example, when replication controllers make API calls to create or delete pods, when [[Jenkins_and_OpenShift#Security_Considerations|Jenkins interacts with the master to start a build, or when an external application makes API calls for monitoring and integration purposes. | ||
A number of service accounts are created automatically when the project is created. The list of service accounts to be created automatically is specified in the [[Master-config.yml#serviceAccountConfig|serviceAccountConfig/managedNames]] section of the OpenShift [[Master-config.yml|master configuration file]]. The list contains "builder", "deployer" and "default". Additional service accounts can also be created by the project administrator, later. | |||
Service accounts provide a way to control API access without sharing [[#Regular_User|regular user]] credentials. Service account authenticated to the API using tokens signed by an internal private RSA key, which is verified by the [[OpenShift Concepts#Authentication_Layer|authentication layer]]. Service accounts can be granted roles like a [[#Regular_User|regular user]], using [[oc policy#add-role-to-user|oc policy add-role-to-user]] command. Every service account is member of the groups "system:service accounts" and "system:serviceaccounts:<project>" and it is given the "system:image-puller" role. The service accounts are represented with the <tt>ServiceAccount</tt> object. Examples: "system:service account:default:deployer" or "system:service account:some-project:builder" | |||
The service accounts for a project can be obtained with [[OpenShift_Security_Operations#Query_Service_Accounts_for_a_Project|oc get sa]] and can be created with [[OpenShift_Security_Operations#Create_a_New_Service_Account|oc create]]. | The service accounts for a project can be obtained with [[OpenShift_Security_Operations#Query_Service_Accounts_for_a_Project|oc get sa]] and can be created with [[OpenShift_Security_Operations#Create_a_New_Service_Account|oc create]]. | ||
Revision as of 21:15, 21 November 2017
External
- https://docs.openshift.com/container-platform/latest/admin_solutions/user_role_mgmt.html
- https://docs.openshift.com/container-platform/latest/architecture/additional_concepts/authentication.html
- https://docs.openshift.com/container-platform/latest/architecture/additional_concepts/authorization.html
Internal
User
Interaction with OpenShift is associated with a user. An OpenShift user is an entity that can make requests to the OpenShift API. Typically, an user represents the account of a developer or administrator. The users are internally represented with an User object, which in turn represents an actor. Permissions can be given to actors in the system by adding roles to them, or their groups. The association between an user or group and a role is called binding. A user/group may be bound to multiple roles.
There are several user types:
Regular User
An individual system user. Regular users are created automatically upon the first login, or they can be created with the API. They are represented with the User object. The regular users on the system can be obtained as "system:admin" with oc get users.
System User
Most system users are created automatically when the infrastructure is defined, for the purpose of enabling the infrastructure to interact with the API securely. System users include:
Cluster Administrator
The cluster administrator 'system:admin'. The cluster administrator has access to everything. It uses a certificate to authenticate with the environment. The certificate is stored in ~/.kube/config file under the Unix account used to connect to the OpenShift environment, in the "users:" section. The original content of ~/.kube/config for the Unix root account of the master server is created by copying it from /etc/origin/master/admin.kubeconfig. This is the procedure allow system:admin to access a remote environment via oc:
Additional users can be made cluster administrators executing oadm policy add-cluter-role-to-user command.
To list the cluster administrators, use oc get clusterrolebinding/cluster-admins command.
Per-Node System User
A per-node user 'system:node:node1.example.com'.
Other System Users
- Users for use by routers.
- Users for use by registries 'system:openshift-registry'
Anonymous System User
An anonymous system user. API requests with missing or invalid authentication are treated as requests from the anonymous system user.
Service Account
A service account is a special, non-human system user that acts automatically and requires access to objects in its own project or other projects. Service accounts are associated with projects (namespace-scoped).
Service accounts are typically used by services such as routers and registries, or when system components need to make an API call to the master: for example, when replication controllers make API calls to create or delete pods, when [[Jenkins_and_OpenShift#Security_Considerations|Jenkins interacts with the master to start a build, or when an external application makes API calls for monitoring and integration purposes.
A number of service accounts are created automatically when the project is created. The list of service accounts to be created automatically is specified in the serviceAccountConfig/managedNames section of the OpenShift master configuration file. The list contains "builder", "deployer" and "default". Additional service accounts can also be created by the project administrator, later.
Service accounts provide a way to control API access without sharing regular user credentials. Service account authenticated to the API using tokens signed by an internal private RSA key, which is verified by the authentication layer. Service accounts can be granted roles like a regular user, using oc policy add-role-to-user command. Every service account is member of the groups "system:service accounts" and "system:serviceaccounts:<project>" and it is given the "system:image-puller" role. The service accounts are represented with the ServiceAccount object. Examples: "system:service account:default:deployer" or "system:service account:some-project:builder"
The service accounts for a project can be obtained with oc get sa and can be created with oc create.
Service accounts and secrets: What is the relationship between service accounts and secrets. What is the semantics of adding a secret to a service account?
User Identity
Information about the identity of users can be obtained with oc get identity. Users are uniquely identified on the system by their UID, but they can have multiple user names associated with them, if they come into the system after being authenticated by different identity providers.
oc get identity NAME IDP NAME IDP USER NAME USER NAME USER UID allow_all:alice allow_all alice alice 2c381dd3-5bbe-11e5-9ccb-08002733d9bd htpasswd:alice htpasswd alice alice2 b19b75ba-5bce-11e5-b065-08002733d9bd
An identity can be deleted with oc delete identity.
User Context
Returned by oc whoami -c.
Group
A group is a set of users. A user can be part of multiple groups. Groups are useful when we want to grant permissions to multiple users at once, versus granting the same permissions to users individually. Groups can be explicitly defined or they can be system groups (virtual groups) that are automatically provisioned by OpenShift.
A group can be associated with multiple roles by binding it to the roles.
Group information can be obtained with oc describe group. A new group can be created with oadm groups.
Virtual Group
system:authenticated - automatically associated with any currently-authenticated users.
system:unauthenticated - automatically associated with any currently-unauthenticated users.
Binding
The association between an user or group and a role is called binding.
For a list of existing cluster role bindings, execute:
oc get clusterrolebinding
Role
Roles
Cluster Roles
A cluster role is a role applicable across all projects. A cluster role is part of the cluster policy.
/basic-user
/cluster-admin
/cluster-reader
/system:registry
The role than needs to be bound to a service account so the service account can operate the integrated registry.
For a complete list of cluster roles, execute:
oc get clusterrolebinding
Local Roles
A local role is a role scoped to a specific project. A local role is part of the project's local policy.
Rule
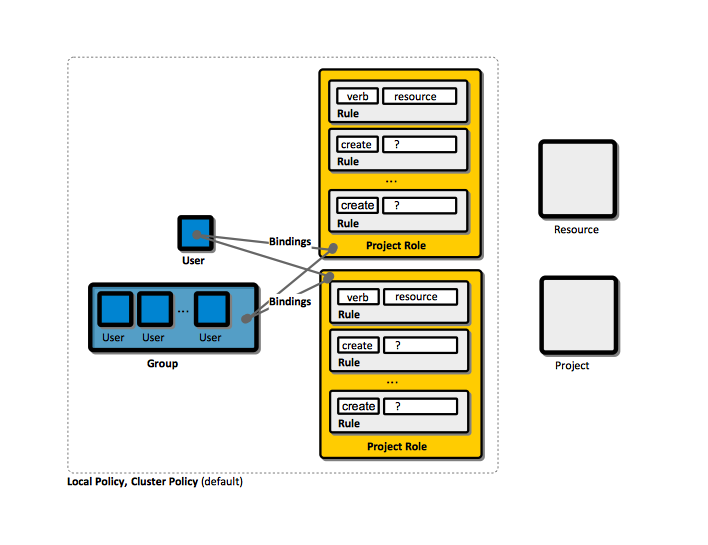
Relationship between Users, Groups, Bindings, Roles and Rules
Policy
A policy is a collection of rules that specify which users can and cannot do with objects (pods, services, etc.). It is a Kubernetes concept.
Cluster Policy
The cluster policy contains roles and bindings that are applicable across all projects. Cluster bindings can only reference cluster roles.
Local Policy
The local policy contains roles and bindings that are scoped to a specific project. Local bindings can reference both cluster roles and local roles.
Authentication
An external user can interact with OpenShift only by making REST API calls. This is how command lines tools, web clients and everybody else interacts with it. Thus the process of authenticating against OpenShift is the process of authenticating against the REST API. Authentication means establishing the identity of the user making the API call. The authentication layer provides a framework for collaboration and quota management. It supports multiple mechanisms for authentication. API calls are authenticated with a token issued by the authentication mechanism. The authentication is performed with oc login.
Authentication Methods
Requests to the OpenShift API are authenticated via two methods:
OAuth Access Tokens
The OpenShift master runs a built-in OAuth server. Users attempting to access the API via CLI or web console must authenticate and obtain an OAuth access token.
The OAuth server can be configured with a pluggable identity provider.
X.509 Client Certificates
Identity Providers
Authorization
TODO: https://home.feodorov.com:9443/wiki/Wiki.jsp?page=OpenShiftAuthorization
Security Context Constraints
OpenShift uses Security Context Constraints (SCCs) to control the actions that a pod can perform and what it has the ability to access.
Secret
A secret resource can hold text or binary secrets for delivery into pods. By default, every container is given a single secret which contains a token for accessing the API with limited privileges, at /var/run/secrets/kubernetes.io/serviceaccount. New secrets can be created and mounted into pods. Secrets from builds can be referenced.
'Secret' operations:
OpenShift Master OAuth Server
The master exposes an OAuth server at "/oauth/authorize".
OAuth Server Configuration
The OAuth server configuration is specified in /etc/origin/master/master-config.yaml, under the "oauthConfig" label.
This is where the OAuth token expiration time can be specified:
accessTokenMaxAgeSeconds: 86400
OpenShift OAuth Authentication Sequence
An OpenShift OAuth token request looks like this:
https://openshift-master1:8443/oauth/authorize?client_id=openshift-challenging-client&response_type=token
with a Basic Authorization header "Authorization: Basic b3ZpZGl1Om92aWRpdTEyMw=="
If authenticated, the response should be a 302 redirect with the Location that contains the token:
Location: https://openshift-master1:8443/oauth/token/display#access_token=Wvgp_89KM-OsOjfQb-wISSfxPFRJdfckAoFMBOrk7Qo&expires_in=86400&token_type=bearer
Note that https://openshift-master1:8443/oauth/token is not actually a redirect location, in that there's nothing there. Explain this.
For more details, see:
OAuthClient
An OAuth client.
OAuth client operations: