AWS Cross-Account Delegation Access: Difference between revisions
| Line 9: | Line 9: | ||
* [[Amazon_AWS_Security_Concepts#Cross-Account_Delegation_Access|AWS Security Concepts]] | * [[Amazon_AWS_Security_Concepts#Cross-Account_Delegation_Access|AWS Security Concepts]] | ||
* [[Amazon_AWS_Security_Concepts#Assuming_a_Role|Assuming a Role]] | |||
=Overview= | =Overview= | ||
Latest revision as of 19:03, 19 August 2020
External
- https://aws.amazon.com/blogs/security/how-to-use-a-single-iam-user-to-easily-access-all-your-accounts-by-using-the-aws-cli/
- https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-account-with-roles.html
- https://aws.amazon.com/blogs/security/how-to-enable-cross-account-access-to-the-aws-management-console/
- https://aws.amazon.com/premiumsupport/knowledge-center/cross-account-access-iam/
Internal
Overview
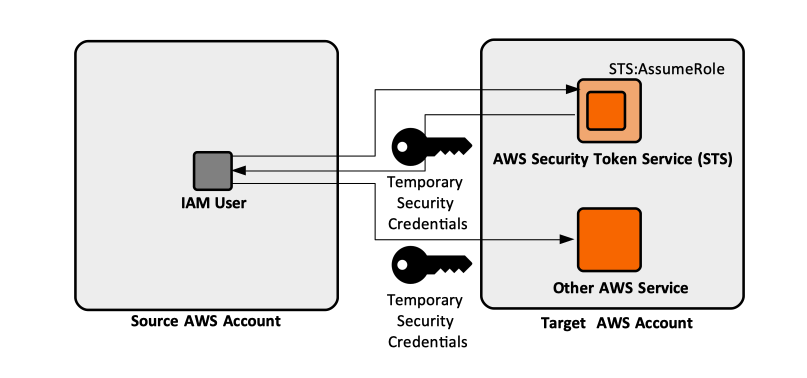
Cross-account delegation access mechanism allows a user that does not have direct access to an AWS account (no IAM user, and no API access key) to perform API calls against resources in the account. Normally, all API calls against the resources of an account are signed with the API access key issued for an IAM user under that account. Cross-account delegation access mechanism leverages temporary AWS security credentials, by using AWS Security Token Service (STS) and IAM roles. This is achieved by making an API call to AWS Security Token Service STS:AssumeRole in the target account. The service returns a temporary access key ID, a secret key and a security token that can then be used to sign future API calls against the target account.
Setting Cross-Account Delegation
TODO, step by step here: https://aws.amazon.com/blogs/security/how-to-use-a-single-iam-user-to-easily-access-all-your-accounts-by-using-the-aws-cli/