Configure mailx to Relay via a Google SMTP Server
Internal
Relevance
mailx 12.5 7/5/10
Overview
This article describes how to configure mailx to send command-line e-mail by relay-ing it via the Google SMTP server.
Create a Dedicated User
This step is optional, but it is a good idea to use a separate "service" account to send service e-mails. The remaining of the example assumes a "service@novaordis.com" was created and it is operational.
Important If the service account was specifically created for this job, you will need to log in at least one time via the web interface (to accept terms and conditions and possibly to change the password), otherwise sending e-mails will fail with "Please log in via your web browser and then try again."
Configure GMail
It is possible to send the e-mail via Google SMTP servers using two mechanisms: GMail SMTP relay service and configuring "Google Apps SMTP settings to send mail from a printer, scanner, or app". This document describes the former. Details on how to use "Google Apps SMTP settings to send mail from a printer, scanner, or app" are available here: https://support.google.com/a/answer/176600?hl=en
Configuring GMail SMTP Relay Service
- Google documentation: SMTP relay service setting https://support.google.com/a/answer/2956491?hl=en
- Troubleshooting: https://support.google.com/a/answer/6140680#maildenied%20ck3sm4780366igb.6
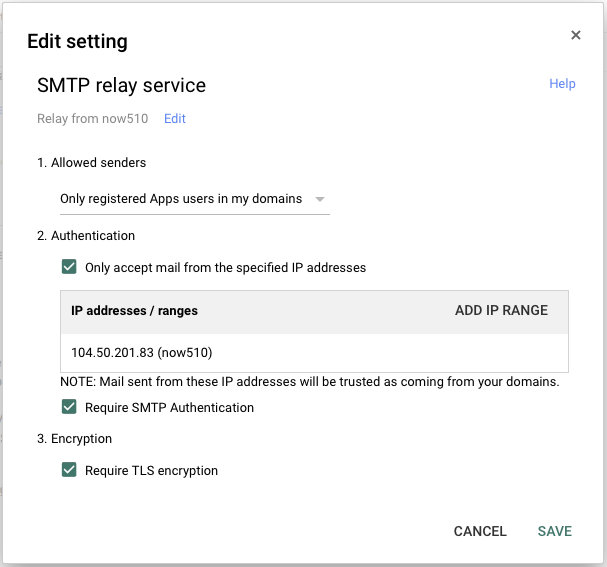
This procedure describes how to configure Google Apps GMail to accept relaying from a specific IP address or set of addresses. Note that is optional, we can solely rely on login authentication, but it is safer.
Google Apps Admin Console -> Apps -> Google Apps -> GMail -> Advanced settings -> "General Settings" tab -> SMTP relay service -> Edit:
Turn on all protection mechanisms available:
- source IP address
- SMTP authentication
- TLS encryption
mailx Configuration
Insure Access to a Valid NSS Certificate Database
You will need to make sure mailx has access to a valid Google certificate in an NSS certificate database. Firefox usually has it in its profile directory, but it is a good idea to initialize a private certificate database. The following page explain how to do that:
This page explains how to "re-use" Firefox Mozilla certificate database:
Assuming you provision root GMail SMTP access, move the certs directory created at the previous step under ~root/etc/certs as follows:
mv .../certs ~root/etc/certs
mail.rc Configuration
Configure /etc/mail.rc as follows:
...
account gmail {
set smtp-auth=login
set smtp=smtps://smtp-relay.gmail.com
set from="service@novaordis.com"
set smtp-auth-user=service@novaordis.com
set smtp-auth-password="PASSWORD"
set ssl-verify=ignore
set nss-config-dir=/root/etc/certs
}
What to Avoid
Do NOT set smtp-use-starttls. If you do that, you'll get:
... >>> STARTTLS 503 5.5.1 bad sequence of commands ck3sm4808076igb.6 - gsmtp smtp-server: 503 5.5.1 bad sequence of commands ck3sm4808076igb.6 - gsmtp
Do NOT use set smtp=smtps://smtp-relay.gmail.com:587, otherwise you'll get:
Resolving host smtp-relay.gmail.com . . . done. Connecting to 173.194.202.28:587 . . . connected. SSL/TLS handshake failed: Unknown error -5938.
mail.rc Permissions
mail.rc contains password, so restrict its permissions:
chmod go-rwx /etc/mail.rc
Test
Still Quite Not All Right
I am getting a certificate error even after using Mozilla's certificates. The e-mail goes through, tough:
[root@now510]# echo "test" | mailx -v -A gmail -s "test" test@example.com Resolving host smtp-relay.gmail.com . . . done. Connecting to 173.194.203.28:smtps . . . connected. Error in certificate: Peer's certificate issuer is not recognized. Comparing DNS name: "smtp-relay.gmail.com" SSL parameters: cipher=AES-128-GCM, keysize=128, secretkeysize=128, issuer=CN=Google Internet Authority G2,O=Google Inc,C=US subject=CN=smtp-relay.gmail.com,O=Google Inc,L=Mountain View,ST=California,C=US 220 smtp-relay.gmail.com ESMTP r8sm1213882igg.3 - gsmtp >>> EHLO now510 250-smtp-relay.gmail.com at your service, [104.50.201.83] 250-SIZE 35882577 250-8BITMIME 250-AUTH LOGIN PLAIN XOAUTH2 PLAIN-CLIENTTOKEN OAUTHBEARER XOAUTH 250-ENHANCEDSTATUSCODES 250-PIPELINING 250-CHUNKING 250 SMTPUTF8 >>> AUTH LOGIN 334 ... >>> ... 334 ... >>> ... 235 2.7.0 Accepted >>> MAIL FROM:<service@....com> 250 2.1.0 OK r8sm1213882igg.3 - gsmtp >>> RCPT TO:<test@example.com> 250 2.1.5 OK r8sm1213882igg.3 - gsmtp >>> DATA 354 Go ahead r8sm1213882igg.3 - gsmtp >>> . 250 2.0.0 OK 1458199638 r8sm1213882igg.3 - gsmtp >>> QUIT 221 2.0.0 closing connection r8sm1213882igg.3 - gsmtp
TODO: try a per-user mail.rc that is read restricted because it contains sensitive credentials.
Test:
echo "mailx e-mail" | mailx -v -A gmail -s "test" somebody@example.com
Deplete:
- http://www.systutorials.com/1411/sending-email-from-mailx-command-in-linux-using-gmails-smtp/
- http://stackoverflow.com/questions/16799407/mailx-and-gmail-nss-config-dir
- http://serverfault.com/questions/498588/smtp-gmail-com-from-bash-gives-error-in-certificate-peers-certificate-issuer
- http://www.systutorials.com/1411/sending-email-from-mailx-command-in-linux-using-gmails-smtp/
- http://serverfault.com/questions/498588/smtp-gmail-com-from-bash-gives-error-in-certificate-peers-certificate-issuer
Next:
- Clarify mail on now510: be able to send mail and test how does cron reacts to it (success or failure). Document -> [1], understand the nss business.