IBM Security Solutions
External
- IBM Tivoli Access Manager WebSEAL overview https://publib.boulder.ibm.com/tividd/td/ITAME/SC32-1359-00/en_US/HTML/am51_webseal_guide10.htm
IBM Tivoli Access Manager
A complete, centralized authorization and network security policy solution solution for distributed applications. It provides security policy management, an authentication framework, an authorization framework, data security and centralized resource management capabilities for a distributed secure domain.
The authentication framework supports built-in authenticators and supports external authenticators.
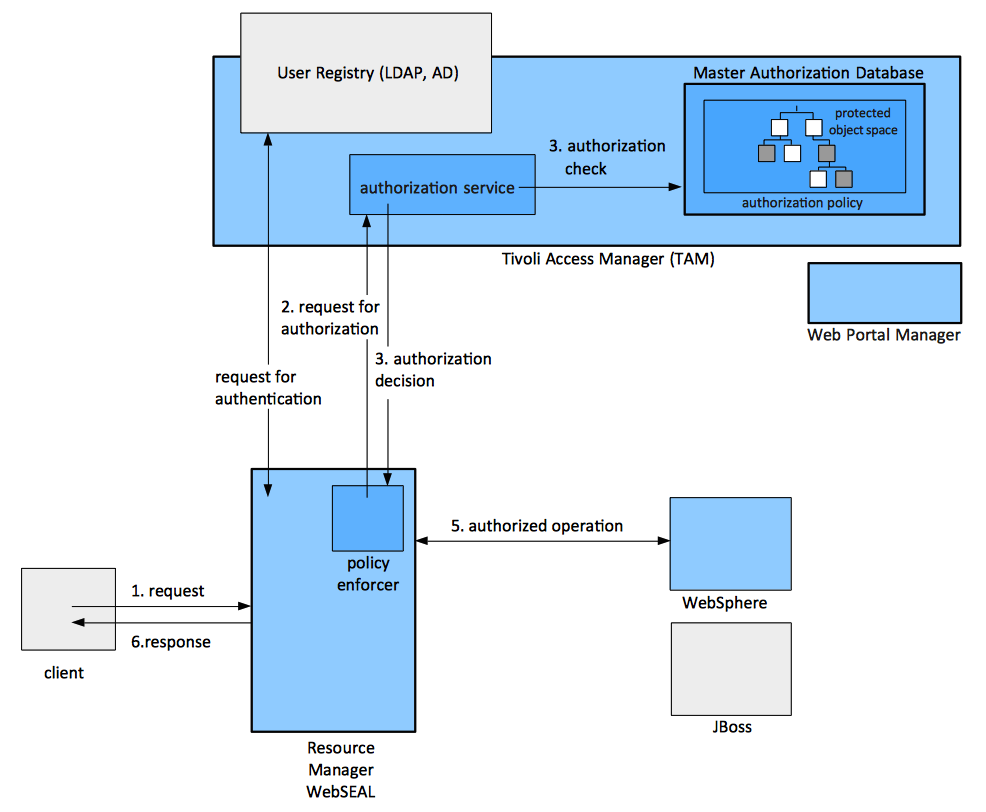
Diagram
Authorization
The authorization service enforces security policies by comparing a user's authentication credentials with the policy permissions assigned to the requested resource. The resulting recommendation is passed to the resource manager (WebSEAL) which completes the response for the original request.
Authorization API
Web Portal Manager
The Web Portal Manager is a Web-based graphical application used to manage security policy in a Tivoli Access Manager secure domain. The pdadmin command line utility provides the same administration capabilities as the Web Portal Manager, plus some commands not supported by the Web Portal Manager. From the Web Portal Manager you can manage the user registry, the master authorization policy database, and the Tivoli Access Manager servers. You can also add and delete users/groups and apply ACL and POP policies to network objects.
WebSEAL
A high-performance, multi-threaded Web server that applies fine-grained security policy to the Tivoli Access Manager-protected Web object space.
WebSEAL can provide single sign-on solutions and incorporate back end Web application server resources into its security policy.
From the perspective of the secure domain topology, WebSEAL acts as a resource manager.
From a functional perspective, WebSEAL acts as a reverse proxy, receiving HTTP/HTTPs requests from browsers and delivering content from its own web servers. Requests passing through WebSEAL are evaluated by the Tivoli Access Manager authorization service to determine whether the user is authenticated and authorized to access the requested resource.
More on protecting the Web space with WebSEAL:
User Authentication
The process of authentication proves the identity of a user to WebSEAL. Only users with an entry in the user registry can become authenticated users.
Credential
When a user successfully authenticates to WebSEAL, a set of identification information known as credential is created for that user. The credential contains the user identity, group membership and any special ("extended") security attributes.
User Registry
The user registry is the user authentication information repository. TAM supports LDAP, Lotus Domino, Microsoft Active Directory. The user registry plays a role in the user authentication process.
Master Authorization Database
The master authorization database contains a representation of all resources in the domain (the protected object space). The security administrator can dictate any level of security by applying rules known as ACL (access control list) policies and protected object policies (POP).
ACL
An access control list (ACL) is the set of rules (permissions) that specifies the conditions necessary to perform certain operations on a specific resource. The ACL policy provide the authorization service with information to make a "yes" or "no" decision on a request to access a protected object and perform some operation on that object. An ACL policy controls:
- What operations can be performed on a resource.
- Who can perform these operations.
An ACL policy is made up of one or more entries that include user and group designators, and their specific permissions or rights. ACLs can also contain rules that apply to unauthenticated users.
POP
POP policies contain additional conditions on the request that are passed back to Tivoli Access Manager Base and the resource manager (such as WebSEAL) along with the "yes" ACL policy decision from the authorization service. It is the responsibility of Tivoli Access Manager and the resource manager to enforce the POP conditions.
More details on POPs
Secure Domain
A set of system resources.
System Resource
A physical file or application being protected as part of the secure domain. The system resource is represented as a protected object in the protected object space.
Protected Object Space
The protected object space is a hierarchical representation of the resources belonging to a Tivoli Access Manager secure domain. Physical network resources from the secure domain are represented as virtual objects in the hierarchical object space.
Protected Object
The logical representation of an actual system resource. Policy templates can be associated to protected objects to provide protection of the resource. The authorization service makes authorization decisions based on these templates. The protected objects can be:
Web Objects
Web objects represent resources that can be addressed by an HTTP URL: static web pages, application URLs, etc. WebSEAL is responsible for protecting Web objects.
Tivoli Access Manager Management Objects
Management objects represent the management activities that can be performed though a Web Portal Manager. The objects represent the tasks necessary to define users and set security policy.
User-Defined Objects
User-defined objects represent customer-defined tasks or network resources protected by applications that access the authorization service through the Tivoli Access Manager authorization API.