Amazon AWS Security Concepts: Difference between revisions
| Line 47: | Line 47: | ||
==IAM ARN== | ==IAM ARN== | ||
==IAM Unique ID== | ==IAM Unique ID== | ||
=IAM Policy= | =IAM Policy= | ||
Revision as of 17:30, 19 November 2019
External
- Understanding and Getting Your Security Credentials https://docs.aws.amazon.com/general/latest/gr/aws-sec-cred-types.html
- Setting Up with Amazon EC2 http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/get-set-up-for-amazon-ec2.html
Internal
Overview
Read this first:
AWS Account
The AWS Account is identified by a 12 digit account ID or an alias. Each AWS account has associated a special sign-in identity that has complete access to all AWS services and resources in the account, called AWS account root user. Each AWS account has its own billing and subscriptions to AWS products. To create an AWS account, go to http://aws.amazon.com, and then click Sign Up. For more details see http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/get-set-up-for-amazon-ec2.html.
AWS Account Root User
The AWS account root user is the special, unique sign-in identity that has complete access to all AWS services and resources in the AWS account.
AWS services require that you provide credentials when you access them. The console requires your password. You can create access keys for your AWS account to access the command line interface or API. However, it is not recommended to access AWS using the credentials for your AWS account root user. Use an IAM user, which is an authenticated identity associated with a person, system, or application who can use AWS products, each with individual security credentials, all controlled by and billed to a single AWS account. The IAM user is provisioned with IAM.
IAM (AWS Identity and Access Management)
AWS Identity and Access Management is a web service that enables AWS customers to manage users and user permissions in AWS. The service is targeted at organizations with multiple users or systems that use AWS products such as Amazon EC2, Amazon RDS, and the AWS Management Console. With IAM, the AWS account root user can can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users can access, and delegate these privileges to other IAM users. In fact, it is recommended practice that AWS account root user creates a corresponding IAM user, which is then used for administrative activities, thus making unnecessary logging in as AWS account root user.
Without IAM, organizations with multiple users and systems must either create multiple AWS accounts, or employees must all share the security credentials of a single AWS account. Also, without IAM, you have no control over the tasks a particular user or system can do and what AWS resources they might use. IAM addresses this issue by enabling organizations to create multiple IAM users.
IAM allows granting different permissions to different people for different resources.
IAM allows generation of credentials for applications that run on EC2 instances. These credentials provide permissions for your application to access other AWS resources, such as S3 buckets or DynamoDB tables.
IAM allows multi-factor authentication (MFA) for the AWS account root user and other individual accounts.
IAM, like many other AWS services, is eventually consistent. IAM achieves high availability by replicating data across multiple servers within Amazon's data centers around the world. If a request to change some data is successful, the change is committed and safely stored. However, the change must be replicated across IAM, which can take some time. Such changes include creating or updating users, groups, roles, or policies.
IAM Identifiers
Friendly Name
Also see path, below.
IAM ARN
IAM Unique ID
IAM Policy
Identity-Based Policies
Identity-based policies are JSON permissions policy documents that can be attached to an identity (user, group, role). These policies control what actions an entity (user or role) can perform, on which resources, and under what conditions. Identity-based policies can be managed policies and inline policies:
Managed Policies
A managed policy is a standalone identity-based policy that can be attached to multiple users, groups, and roles in an AWS account. There are two types of managed policies:
AWS Managed Policies
Managed policies that are created and managed by AWS. The ARN of a policy that is managed by AWS is:
arn:aws:iam::aws:policy/PolicyName
Customer Managed Policies
Customer managed policies are managed policies create and manage by users in an AWS account. Customer managed policies provide more precise control over policies than AWS managed policies. IAM policy can be created and edited in a visual editor or by creating the JSON policy document directly. Once created, policies are referenced by their ARNs. The ARN of a customer-managed policy is:
arn:aws:iam::AWS-account-number:policy/PolicyName
Operations:
Inline Policies
Policies created by users and that are embedded directly into a single user, group, or role. In most cases, inline policies usage is not recommended:
Resource-Based Policies
Difference between Identity-Based Policies and Resource-Based Policies
IAM Permissions Boundaries
Service Control Policies (SCPs)
Access Control Policies (ACLs)
Session Policies
API Access Keys
Each IAM user has a set of API access keys. These keys are needed when the user attempts to make programmatic calls to AWS or EC2, using Amazon EC2 CLI tools for example. The user can create, modify, view and rotate these access keys.
There are two types of access keys:
- Access key ID (example AKIAIOSFODNN7EXAMPLE))
- Secret access key (example: wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY)
When creating an access key, IAM returns the access key id and the secret access key. The secret access key is only accessible at the time it was created. If the secret access key is lost, the corresponding access key must be deleted and recreated.
Relationship between Access Key ID and Secret Key?
The access keys can be managed here: https://console.aws.amazon.com/iam/home?#security_credential by navigating to Users -> username -> Security Credentials -> Access Credentials.
More about access keys for IAM users: http://docs.aws.amazon.com/IAM/latest/UserGuide/ManagingCredentials.html
For details on how access keys can be set in the local environment, see Setting the Access Keys during Amazon EC2 CLI Installation.
AWS Credentials
AWS credentials can be set as explained here:
Access Key ID
Secret Key ID
Session Token
Credentials Profile
TODO: https://docs.aws.amazon.com/sdk-for-java/v2/developer-guide/credentials.html
MFA Multi Factor Authentication
Instance Access Key Pairs
Amazon AWS uses public-key cryptography to secure the login to instances. The instance has no password - you use a key pair to access your instance securely. The key pairs are provisioned either via the web interface or with Amazon CLI tools. During the provisioning process, the keys pairs are named. When the instance is created, you need to specify the name of the key pair to use to protect access to it: Amazon will install the public certificate in ~/.ssh/authorized_keys when creating the instance, and then you need to provide the private key of the pair to your ssh client when logging into the instance.
External reference: http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-key-pairs.html
This is the procedure to create a key pair.
Security Group
- Amazon EC2 Security Groups for Linux Instances https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html
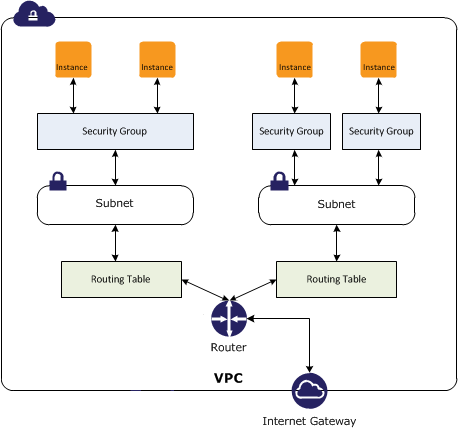
A security group acts as a virtual firewall for instances. The security group controls inbound and outbound traffic. You can specify one or more security groups when you launch an instance. A security group contains a set of rules that control the inbound traffic and a different set of rules that control the outbound traffic. All other traffic is discarded.
The rules can be modify at any time; the new rules are automatically enforced - it is sufficient to add a new rule with the CLI or via the management interface and the rule takes effect immediately, without requiring instance reboots.