Amazon VPC Concepts: Difference between revisions
| (74 intermediate revisions by the same user not shown) | |||
| Line 10: | Line 10: | ||
[[#Virtual_Private_Cloud_.28VPC.29|Amazon VPC]] provides a logically isolated section of the AWS Cloud where AWS resources run in a private virtual network. | [[#Virtual_Private_Cloud_.28VPC.29|Amazon VPC]] provides a logically isolated section of the AWS Cloud where AWS resources run in a private virtual network. | ||
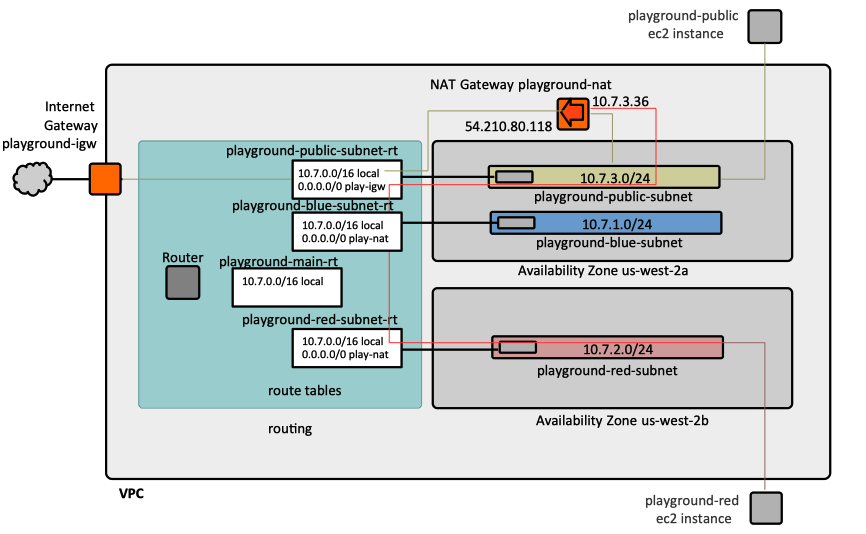
:[[File:AmazonVPC.png]] | |||
VPCs are essential to [[Amazon_EC2_Concepts#Overview|EC2-VPC]], which is an Amazon Elastic Compute Cloud platform that is aimed at launching AWS resources into a VPC. | |||
=<span id='VPC'></span>Virtual Private Cloud (VPC)= | =<span id='VPC'></span>Virtual Private Cloud (VPC)= | ||
| Line 15: | Line 19: | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-ip-addressing.html VPC IP Addressing]}} | {{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-ip-addressing.html VPC IP Addressing]}} | ||
A VPC is a virtual network dedicated to an AWS account and logically isolated from other virtual networks in the AWS Cloud. It can be thought of as an isolated portion of the AWS Cloud populated with private AWS resources, such as Fargate tasks. The VPC has a [[#Primary_CIDR_Block|primary IP address range]], specified as a | A VPC is a virtual network dedicated to an AWS account and logically isolated from other virtual networks in the AWS Cloud. It can be thought of as an isolated portion of the AWS Cloud populated with private AWS resources, such as Fargate tasks. VPC allows direct control over the networking environment: selecting IP address ranges, creating subnets, configuring routing and access control lists. | ||
The VPC has a [[#Primary_CIDR_Block|primary IP address range]], specified as a '''CIDR Block''', such as 10.0.0.0/16 or 10.7.0.0/16. Block sizes must be between /16 netmask and /28 netmask. More details about the [[IP_Address#The_CIDR_.28Classless_Inter-Domain_Routing.29_Notation|CIDR]]. | |||
A | A VPC uses [[#Subnet|subnets]], [[#Route_Table|route tables]] and [[#Security_Group|security groups]] to segregate and route IP traffic. Each VPN has a default router configured based on the [[#VPC_Main_Route_Table|main route table]]. | ||
<span id='VPC_and_Availability_Zones'></span><span id='Availability_Zone'></span>A VPC spans all [[Amazon_AWS_Concepts#Availability_Zones|availability zones]] in a [[Amazon_AWS_Concepts#Region|region]]. A VPC cannot span multiple [[Amazon_AWS_Concepts#Region|regions]]. A [[#Subnet|subnet]] can belong to one and only one availability zone. | <span id='VPC_and_Availability_Zones'></span><span id='Availability_Zone'></span>A VPC spans all [[Amazon_AWS_Concepts#Availability_Zones|availability zones]] in a [[Amazon_AWS_Concepts#Region|region]]. A VPC cannot span multiple [[Amazon_AWS_Concepts#Region|regions]]. A [[#Subnet|subnet]] can belong to one and only one availability zone. | ||
External access to internet can be provided by configuring an [[#Internet_Gateway|internet gateway]]. The VPC can be connected to a VPN with a [[#Virtual_Private_Gateway|virtual private gateway]]. | External access to internet can be provided by configuring an [[#Internet_Gateway|internet gateway]]. The VPC can be connected to a VPN with a [[#Virtual_Private_Gateway|virtual private gateway]]. | ||
The full list of resources that are associated (internal) to a VPC and that get deleted if the VPC containing them is deleted is: | |||
* Subnets | |||
* Security Groups | |||
* Network ACLs | |||
* Internet Gateways | |||
* Egress Only Internet Gateways | |||
* Route Tables | |||
* Network Interfaces | |||
* Peering Connections | |||
* Endpoints | |||
==VPC ID== | ==VPC ID== | ||
==VPC Name== | |||
The name of the VPC can be specified by setting the "Name" tag, as shown [[Amazon_VPC_Operations#Create_a_VPC_with_CloudFormation|here]]. | |||
==<span id='Primary_CIDR_Block'></span>Primary IP Address Range (CIDR Block)== | ==<span id='Primary_CIDR_Block'></span>Primary IP Address Range (CIDR Block)== | ||
| Line 34: | Line 54: | ||
==Tenancy== | ==Tenancy== | ||
The instance tenancy can be "default" or "dedicated". The default behavior is that instances can be launched with any tenancy. If the tenancy is configured as "dedicated", any instance launched into the VPC automatically has dedicated tenancy, unless it was explicitly launched with the default tenancy. Note that updating instance tenancy from "default" to "dedicated" requires replacement of the VPC. | |||
==<span id='Network_Interface'></span>Elastic Network Interface (ENI)== | ==<span id='Network_Interface'></span>Elastic Network Interface (ENI)== | ||
| Line 44: | Line 66: | ||
{{External|[https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/elastic-ip-addresses-eip.html Elastic IP Addresses]}} | {{External|[https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/elastic-ip-addresses-eip.html Elastic IP Addresses]}} | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-ip-addressing.html IP Addressing in Your VPC]}} | |||
An Elastic IP address is a public IPv4 address, which is reachable from the internet. If an EC2 instance is associated with an Elastic IP, that instance can communicate with the internet. With an Elastic IP address, the failure of an instance or a service can be masked by rapidly remapping the address to another instance in the same account. An elastic IP address seems to be a public routable address from Amazon's pool and logic to adjust VPC routing dynamically: the elastic IPv4 address is accessed through the internet gateway of your VPC. An elastic IP address can be associated with only one resource at a time, so if it is associated with another resource, it must first disassociate it: think of elastic IP addresses as resources that have to be provisioned and must be released, reused and deleted when they're not needed anymore. | |||
Elastic IP addresses are used by: | |||
* [[#Elastic_IP_Allocation|NAT Gateways]] | |||
* <span id='Elastic_IP_Address_EC2_Instance'></span>[[Amazon_EC2_Concepts#Elastic_IP_and_EC2_Instances|EC2 Instances]] | |||
===Publicly Routable IP Address=== | |||
===Scope=== | |||
"vpc" for VPC elastic IP addresses. | |||
===Allocation ID=== | |||
The allocation ID is an attribute of an elastic IP address assigned by AWS, representing the allocation of the address for use a [[#VPC|VPC]]. This attribute has values only for VPC elastic IP addresses. The allocation ID can be obtained from the elastic IP address in CloudFormation templates with: | |||
AllocationId: ![[AWS_CloudFormation_Concepts_Intrinsic_Functions#GetAtt|GetAtt]] MyElasticIP.AllocationId | |||
===Association ID=== | |||
===Private IP Address=== | |||
===Network Interface ID=== | |||
===Network Interface Owner ID=== | |||
===Elastic IP Address Operations=== | |||
* [[Amazon_VPC_Operations#Create_an_Elastic_IP_with_CloudFormation|Create an Elastic IP Address with CloudFormation]] | |||
==DNS== | |||
A VPC has the capability to resolve DNS addresses. This capability is configured when the VPC is created, and can be updated without interruption after that. If the option to resolve DNS names is turned on, the Amazon DNS server resolves DNS hostnames for instances deployed in the VPC. | |||
===DNS Hostname Generation=== | |||
Instances launched in a VPC may get hostnames, if the capability is explicitly configured (by default, it is not). The capability can be turned on only if [[#DNS|DNS support]] is enabled. | |||
==VPC Operations== | ==VPC Operations== | ||
* [[Amazon_VPC_Operations#Describe_VPC|Describe VPC]] | * [[Amazon_VPC_Operations#Describe_VPC|Describe VPC]] | ||
* [[Amazon_VPC_Operations#Create_a_VPC_with_Amazon_Console|Create a VPC with Amazon Console]] | |||
* [[Amazon_VPC_Operations#Create_a_VPC_with_CloudFormation|Create a VPC with CloudFormation]] | |||
=CIDR Block= | |||
Aside from the [[Amazon_VPC_Concepts#Primary_IP_Address_Range_.28CIDR_Block.29|primary CIDR block]], VPCs can have additional CIDR blocks associated with them. The CIDR blocks associated with a VPC can be obtained [[Amazon_VPC_Operations#Describe_VPC|describing the VPC]]: | |||
<syntaxhighlight lang='json'> | |||
{ | |||
"VpcId": "vpc-09999999999999999", | |||
"CidrBlock": "10.2.0.0/16", | |||
[...] | |||
"CidrBlockAssociationSet": [ | |||
{ | |||
"AssociationId": "vpc-cidr-assoc-09999999999999999", | |||
"CidrBlock": "10.2.0.0/16", | |||
"CidrBlockState": { | |||
"State": "associated" | |||
} | |||
}, | |||
{ | |||
"AssociationId": "vpc-cidr-assoc-08888888888888888", | |||
"CidrBlock": "10.20.0.0/16", | |||
"CidrBlockState": { | |||
"State": "associated" | |||
} | |||
} | |||
], | |||
... | |||
} | |||
</syntaxhighlight> | |||
==CIDR Block Operations== | |||
* [[Amazon_VPC_Operations#Disassociate_a_CIDR_Block_from_VPC|Disassociate a CIDR Block from VPC]] | |||
=Subnet= | =Subnet= | ||
A subnet is a range of IP addresses in the [[#VPC|Virtual Private Cloud (VPC)]] that can be used to isolate different EC2 resources or ECS services from each other, within the same VPC, or from the Internet. | A subnet is a range of IP addresses in the [[#VPC|Virtual Private Cloud (VPC)]] that can be used to isolate different EC2 resources or ECS services from each other, within the same VPC, or from the Internet. Subnets enable you to group instances based on security and operational needs. Each subnet can belong to one and only one [[#VPC|VPC]]. Each subnet can belong to one and only one [[#Availability_Zone|availability zone]], and it cannot span zones. The availability zone can be specified when the subnet is created, but it is not required. If not specified, AWS will select an availability zone. The documentation says this is the recommended behavior. However, we found that if we let AWS pick the availability zone, two subnets might end in the same availability zone, and if there's an [[AWS_Elastic_Load_Balancing_Concepts#Application_Load_Balancer|application load balancer]] that uses those subnets, the application load balancer will fail to start. For this reason, we prefer to explicitly select availability zones. Each subnet has a [[#Subnet_ID|subnet ID]]: <tt>subnet-53993c24: 172.31.16.0/20</tt>. | ||
Each subnet has a [[#Subnet_ID|subnet ID]]: <tt>subnet-53993c24: 172.31.16.0/20</tt>. | |||
The range of IP addresses in the subnet must be a subset of the [[#Primary_IP_Address_Range_.28CIDR_Block.29|VPC primary IP range]], otherwise it is said that [[IP_Address#In_Range|the subnet is not within range]] of the VPC CIDR. Block sizes must be between /16 netmask and /28 netmask. The size of the subnet can equal the size of the VPC. | |||
To enable instances in a subnet to reach the Internet and AWS services, you must add an [[#Internet_Gateway|Internet gateway]] to the [[#VPC|VPC]] and a [[#Route_Table|route table]] with a route to the Internet to the subnet. It is also possible to allow an instance hosted in the VPC to initiate outbound connections to the internet over IPv4 but prevent unsolicited inbound connection from the internet, by using a NAT gateway. The IPv6 equivalent is an [[Amazon_VPC_Concepts#Egress_Only_Internet_Gateway|Egress-only internet gateway]]. | To enable instances in a subnet to reach the Internet and AWS services, you must add an [[#Internet_Gateway|Internet gateway]] to the [[#VPC|VPC]] and a [[#Route_Table|route table]] with a route to the Internet to the subnet. It is also possible to allow an instance hosted in the VPC to initiate outbound connections to the internet over IPv4 but prevent unsolicited inbound connection from the internet, by using a NAT gateway. The IPv6 equivalent is an [[Amazon_VPC_Concepts#Egress_Only_Internet_Gateway|Egress-only internet gateway]]. | ||
| Line 70: | Line 145: | ||
==Relationship between VPC and Subnets== | ==Relationship between VPC and Subnets== | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/how-it-works.html#how-it-works-subnet How Does a Subnet Work?]}} | |||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html VPC and Subnets]}} | {{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Subnets.html VPC and Subnets]}} | ||
| Line 89: | Line 165: | ||
===Private Subnet=== | ===Private Subnet=== | ||
If a subnet does not have a route in its explicitly associated [[#VPC_Main_Route_Table|route table]] or, if not implicitly associated, in the [[#VPC_Main_Route_Table|VPC main route table]] to an [[#Internet_Gateway|internet gateway]], it is known as a private subnet. Usually the route to the gateway is 0.0.0.0/0. | If a subnet does not have a route in its explicitly associated [[#VPC_Main_Route_Table|route table]] or, if not implicitly associated, in the [[#VPC_Main_Route_Table|VPC main route table]] to an [[#Internet_Gateway|internet gateway]], it is known as a private subnet. Usually the route to the gateway is 0.0.0.0/0. Subnets that have routes to NAT gateways are still considered private subnets. An instance in a private subnet is not publicly accessible even if it has an Elastic IP address or a public IP address associated with it, because the IP address is not routed to the subnet. | ||
===VPN-Only Subnet=== | ===VPN-Only Subnet=== | ||
| Line 107: | Line 183: | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html Network ACLs]}} | {{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html Network ACLs]}} | ||
Network ACLs control inbound and outbound traffic for subnets. Each subnet must be associated with a network ACL. | Network ACLs control inbound and outbound traffic for subnets. Each subnet must be associated with a network ACL. | ||
==Mapping Public IP Addressed on Launch== | |||
A subnet can be configured so instances that are launched in this subnet receive a public IP address. By default, the behavior is turned off. | |||
==Subnet Operations== | |||
* [[Amazon_VPC_Operations#Create_a_Subnet_with_CloudFormation|Create a Subnet with CloudFormation]] | |||
=Route Table= | =Route Table= | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html Route Tables]}} | {{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html Route Tables]}} | ||
A route table is a set of rules, called routes, that are used to determine where network traffic is directed. A subnet must be associated with one and only one route table, but one route table can be associated with multiple subnets. If no route table is explicitly associated with the subnet, the subnet is implicitly associated with the [[#VPC_Main_Route_Table|VPC main route table]]. It is said to be implicitly associated because the [[#VPC_Main_Route_Table|VPC main route table]] does not list the subnet amongst those subnets it was explicitly associated with. It does show it in a separated list, with the following caption "the following subnets have not been explicitly associated with any route tables and are therefore associated with the main route table". | A route table is a set of rules, called routes, that are used to determine where network traffic is directed. Each route specifies a destination CIDR and a target - the most specific routes that match are used to determine how to route the traffic. This is called "the longest prefix match" rule. Every route table contains a local route for communication within the VPC over IPv4. If the VPC has more than one IPv4 CIDR block, the route tables contain a local route for each IPv4 CIDR block. | ||
A subnet must be associated with one and only one route table, but one route table can be associated with multiple subnets. If no route table is explicitly associated with the subnet, the subnet is implicitly associated with the [[#VPC_Main_Route_Table|VPC main route table]]. It is said to be implicitly associated because the [[#VPC_Main_Route_Table|VPC main route table]] does not list the subnet amongst those subnets it was explicitly associated with. It does show it in a separated list, with the following caption "the following subnets have not been explicitly associated with any route tables and are therefore associated with the main route table". | |||
The subnet's route table, whichever it is, controls routing for the subnet. | |||
Any route table comes with the a rule similar to: | Any route table comes with the a rule similar to: | ||
| Line 118: | Line 206: | ||
The rule lists the [[#Primary_IP_Address_Range_.28CIDR_Block.29|primary IP address range of the VPC]], as a CIDR block, with a "local" target. This rule cannot be deleted. This rule means that any subnet will be routed by default to any subnet within the VPC. | The rule lists the [[#Primary_IP_Address_Range_.28CIDR_Block.29|primary IP address range of the VPC]], as a CIDR block, with a "local" target. This rule cannot be deleted. This rule means that any subnet will be routed by default to any subnet within the VPC. | ||
CIDR blocks for IPv4 and IPv6 are treated separately. For example, a route with a destination CIDR of 0.0.0.0/0 (all IPv4 addresses) does not automatically include all IPv6 addresses. You must create a route with a destination CIDR of ::/0 for all IPv6 addresses. | |||
==VPC Main Route Table== | ==VPC Main Route Table== | ||
The VPC main route table is the default route table for the VPC - all VPC subnets are implicitly associated with it, unless they are explicitly associated with other route tables. The routes in the main route table can be modified. | The VPC main route table is the default route table for the VPC - all VPC subnets are implicitly associated with it, unless they are explicitly associated with other route tables. The routes in the main route table can be modified. One way to protect a VPC is to leave the main route table in its original default state, with only the local route, and explicitly associate each new subnet with custom route tables. This gives control over how each subnet routes outbound traffic. | ||
===Main Router=== | ===Main Router=== | ||
| Line 128: | Line 220: | ||
=Gateways= | =Gateways= | ||
When an Internet gateway, an egress-only Internet gateway, a virtual private gateway, a NAT device, a peering connection, or a VPC endpoint is added in the VPC, the [[#Route_Table|route table]] for any subnet that uses these gateways or connections must be updated. | |||
==<span id='Gateway'></span><span id='Network_Gateway'></span>Internet Gateway== | ==<span id='Gateway'></span><span id='Network_Gateway'></span>Internet Gateway== | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html#route-tables-internet-gateway Route Tables for an Internet Gateway]}} | |||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Internet_Gateway.html Internet Gateways]}} | |||
An internet gateway enables communication over the internet. An internet gateway is attached to the [[#VPC|VPC]]. | An internet gateway enables communication over the internet. An internet gateway is attached to the [[#VPC|VPC]]. | ||
== | To give a subnet access to internet, add a route with a destination of 0.0.0.0/0 for IPv4 traffic or ::/0 for IPv6 traffic, and a target of the Internet gateway ID (igw-xxxxxxxx). | ||
===VPC-Gateway Attachment=== | |||
An internet gateway is not attached with any VPC after creation, an AWS::EC2::VPCGatewayAttachment resource must be created to attach the internet gateway to a VPC. | |||
===Internet Gateway Operations=== | |||
* [[Amazon_VPC_Operations#Create_an_Internet_Gateway|Create an Internet Gateway]] | |||
==NAT Gateway== | ==NAT Gateway== | ||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html#route-tables-nat Route Tables for a NAT Device]}} | |||
{{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-gateway.html NAT Gateways]}} | {{External|[https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-gateway.html NAT Gateways]}} | ||
NAT Gateways provide external access for private subnets. For example, if ECS tasks are running in private subnets, external access needs to be added so the task can pull the associated container images from their corresponding ECR repositories. | NAT Gateways provide external access for private subnets. For example, if ECS tasks are running in private subnets, external access needs to be added so the task can pull the associated container images from their corresponding ECR repositories. One way to enable external access, without allowing unsolicited inbound connections is to create and use a NAT gateway. To enable instances in a private subnet to connect to the Internet, you can create a NAT gateway or launch a NAT instance in a public subnet, and then add to the route table associated with the private subnet a route that routes IPv4 Internet traffic (0.0.0.0/0) to the NAT device. | ||
===Elastic IP=== | |||
A NAT gateway must be associated an [[#Elastic_IP_Address|elastic IP address]], which is routable on the Internet. Even if the NAT gateway gets its elastic IP address, it still needs to be deployed behind an internet gateway so that public IP address is '''routed'''. That means the NAT must be deployed in a public subnet, has the routing configured to route the elastic IP of the NAT gateway externally to the internet. The private subnets that want unidirectional outbound internet connectivity will route to the NAT gateway. The NAT gateway is reachable over its private IP address, which is routed - and reachable - inside the VPC. | |||
The NAT is associated with the elastic IP in CloudFormation using the "AllocationId" attribute, as follows: | |||
Resources: | |||
NATGateway: | |||
Type: AWS::EC2::NatGateway | |||
Properties: | |||
... | |||
AllocationId: !Ref ElasticIP | |||
===NAT Gateway Operations=== | ===NAT Gateway Operations=== | ||
* [[Create a NAT Gateway with Amazon Console]] | * [[Create a NAT Gateway with Amazon Console]] | ||
==Egress Only Internet Gateway== | |||
The IPv6 equivalent of NAT gateway. | |||
==Virtual Private Gateway== | ==Virtual Private Gateway== | ||
| Line 158: | Line 278: | ||
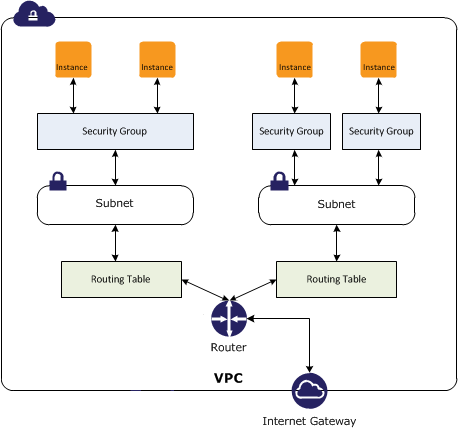
==Security Group== | ==Security Group== | ||
* Amazon EC2 Security Groups for Linux Instances https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html | |||
A ''security group'' acts as a virtual firewall for instances. The security group controls inbound and outbound traffic. You can specify one or more security groups when you launch an instance. A security group contains a set of ''rules'' that control the inbound traffic and a different set of ''rules'' that control the outbound traffic. All other traffic is discarded. | |||
The rules can be modify at any time; the new rules are automatically enforced - it is sufficient to add a new rule with the CLI or via the management interface and the rule takes effect immediately, without requiring instance reboots. | |||
[[Image:security_group.png|center]] | |||
There is an upper limit for both inbound rules (60) and outbound rules per security group. The limit can be changed through the [[AWS Service Quotas|Service Quotas]] service by navigating to Service Quotas → AWS services → Amazon Virtual Private Cloud (Amazon VPC) → Inbound or outbound rules per security group. | |||
===Security Group ID=== | |||
===Security Group Operations=== | |||
* [[AWS Security Operations#Create_a_Security_Group|Create a security group]] | |||
* [[AWS Security Operations#List_the_Security_Groups|List the existing security groups]] | |||
==Network Access Control List (ACL)== | ==Network Access Control List (ACL)== | ||
| Line 180: | Line 316: | ||
To use private hosted zones, set [[#enableDnsHostnames| enableDnsHostnames]] and [[#enableDnsSupport|enableDnsSupport]] to true when creating the VPC. Also see: {{Internal|Amazon_Route53_Concepts#Private_Hosted_Zone_for_Amazon_VPC|Private Hosted Zone}} | To use private hosted zones, set [[#enableDnsHostnames| enableDnsHostnames]] and [[#enableDnsSupport|enableDnsSupport]] to true when creating the VPC. Also see: {{Internal|Amazon_Route53_Concepts#Private_Hosted_Zone_for_Amazon_VPC|Private Hosted Zone}} | ||
=VPC Quotas and Limits= | |||
{{External|https://docs.aws.amazon.com/vpc/latest/userguide/amazon-vpc-limits.html}} | |||
=PrivateLink= | |||
{{External|https://docs.aws.amazon.com/vpc/latest/privatelink/endpoint-service.html}} | |||
{{External|https://docs.aws.amazon.com/whitepapers/latest/aws-privatelink/aws-privatelink.html}} | |||
AWS PrivateLink provides secure, private connectivity between Amazon VPCs, AWS services, and on-premises applications, using the the private AWS network. | |||
==<span id='VPC_Endpoint'></span>VPC Endpoints== | |||
{{External|https://docs.aws.amazon.com/whitepapers/latest/aws-privatelink/what-are-vpc-endpoints.html}} | |||
A VPC endpoint enables customers to privately connect to supported AWS services and VPC endpoint services relying on AWS PrivateLink. Amazon VPC instances do not require public IP addresses to communicate with resources of the service. Traffic between an Amazon VPC and a service does not leave the Amazon network. | |||
==Relationship between Direct Connect and PrivateLink== | |||
{{Internal|AWS_Direct_Connect_Concepts#Relationship_between_Direct_Connect_and_PrivateLink|AWS Direct Connect Concepts | Relationship between Direct Connect and PrivateLink}} | |||
Latest revision as of 01:40, 17 January 2023
External
Internal
Overview
Amazon VPC provides a logically isolated section of the AWS Cloud where AWS resources run in a private virtual network.
VPCs are essential to EC2-VPC, which is an Amazon Elastic Compute Cloud platform that is aimed at launching AWS resources into a VPC.
Virtual Private Cloud (VPC)
A VPC is a virtual network dedicated to an AWS account and logically isolated from other virtual networks in the AWS Cloud. It can be thought of as an isolated portion of the AWS Cloud populated with private AWS resources, such as Fargate tasks. VPC allows direct control over the networking environment: selecting IP address ranges, creating subnets, configuring routing and access control lists.
The VPC has a primary IP address range, specified as a CIDR Block, such as 10.0.0.0/16 or 10.7.0.0/16. Block sizes must be between /16 netmask and /28 netmask. More details about the CIDR.
A VPC uses subnets, route tables and security groups to segregate and route IP traffic. Each VPN has a default router configured based on the main route table.
A VPC spans all availability zones in a region. A VPC cannot span multiple regions. A subnet can belong to one and only one availability zone.
External access to internet can be provided by configuring an internet gateway. The VPC can be connected to a VPN with a virtual private gateway.
The full list of resources that are associated (internal) to a VPC and that get deleted if the VPC containing them is deleted is:
- Subnets
- Security Groups
- Network ACLs
- Internet Gateways
- Egress Only Internet Gateways
- Route Tables
- Network Interfaces
- Peering Connections
- Endpoints
VPC ID
VPC Name
The name of the VPC can be specified by setting the "Name" tag, as shown here.
Primary IP Address Range (CIDR Block)
When the VPC is created, a range of IPv4 addresses in the form of a Classless Inter-Domain Routing (CIDR) block must be provided for the VPC. This is the primary CIDR block for the VPC. Example: 10.0.0.0/16.
Default VPC
Only one VPC per account is the default VPC.
Tenancy
The instance tenancy can be "default" or "dedicated". The default behavior is that instances can be launched with any tenancy. If the tenancy is configured as "dedicated", any instance launched into the VPC automatically has dedicated tenancy, unless it was explicitly launched with the default tenancy. Note that updating instance tenancy from "default" to "dedicated" requires replacement of the VPC.
Elastic Network Interface (ENI)
A VPC cannot be deleted if a network interface attached to it is in use.
Elastic IP Address
An Elastic IP address is a public IPv4 address, which is reachable from the internet. If an EC2 instance is associated with an Elastic IP, that instance can communicate with the internet. With an Elastic IP address, the failure of an instance or a service can be masked by rapidly remapping the address to another instance in the same account. An elastic IP address seems to be a public routable address from Amazon's pool and logic to adjust VPC routing dynamically: the elastic IPv4 address is accessed through the internet gateway of your VPC. An elastic IP address can be associated with only one resource at a time, so if it is associated with another resource, it must first disassociate it: think of elastic IP addresses as resources that have to be provisioned and must be released, reused and deleted when they're not needed anymore.
Elastic IP addresses are used by:
Publicly Routable IP Address
Scope
"vpc" for VPC elastic IP addresses.
Allocation ID
The allocation ID is an attribute of an elastic IP address assigned by AWS, representing the allocation of the address for use a VPC. This attribute has values only for VPC elastic IP addresses. The allocation ID can be obtained from the elastic IP address in CloudFormation templates with:
AllocationId: !GetAtt MyElasticIP.AllocationId
Association ID
Private IP Address
Network Interface ID
Network Interface Owner ID
Elastic IP Address Operations
DNS
A VPC has the capability to resolve DNS addresses. This capability is configured when the VPC is created, and can be updated without interruption after that. If the option to resolve DNS names is turned on, the Amazon DNS server resolves DNS hostnames for instances deployed in the VPC.
DNS Hostname Generation
Instances launched in a VPC may get hostnames, if the capability is explicitly configured (by default, it is not). The capability can be turned on only if DNS support is enabled.
VPC Operations
CIDR Block
Aside from the primary CIDR block, VPCs can have additional CIDR blocks associated with them. The CIDR blocks associated with a VPC can be obtained describing the VPC:
{
"VpcId": "vpc-09999999999999999",
"CidrBlock": "10.2.0.0/16",
[...]
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-09999999999999999",
"CidrBlock": "10.2.0.0/16",
"CidrBlockState": {
"State": "associated"
}
},
{
"AssociationId": "vpc-cidr-assoc-08888888888888888",
"CidrBlock": "10.20.0.0/16",
"CidrBlockState": {
"State": "associated"
}
}
],
...
}
CIDR Block Operations
Subnet
A subnet is a range of IP addresses in the Virtual Private Cloud (VPC) that can be used to isolate different EC2 resources or ECS services from each other, within the same VPC, or from the Internet. Subnets enable you to group instances based on security and operational needs. Each subnet can belong to one and only one VPC. Each subnet can belong to one and only one availability zone, and it cannot span zones. The availability zone can be specified when the subnet is created, but it is not required. If not specified, AWS will select an availability zone. The documentation says this is the recommended behavior. However, we found that if we let AWS pick the availability zone, two subnets might end in the same availability zone, and if there's an application load balancer that uses those subnets, the application load balancer will fail to start. For this reason, we prefer to explicitly select availability zones. Each subnet has a subnet ID: subnet-53993c24: 172.31.16.0/20.
The range of IP addresses in the subnet must be a subset of the VPC primary IP range, otherwise it is said that the subnet is not within range of the VPC CIDR. Block sizes must be between /16 netmask and /28 netmask. The size of the subnet can equal the size of the VPC.
To enable instances in a subnet to reach the Internet and AWS services, you must add an Internet gateway to the VPC and a route table with a route to the Internet to the subnet. It is also possible to allow an instance hosted in the VPC to initiate outbound connections to the internet over IPv4 but prevent unsolicited inbound connection from the internet, by using a NAT gateway. The IPv6 equivalent is an Egress-only internet gateway.
A subnet has a route table.
Relationship between VPC and Subnets
VPC Main route table and any custom route table contain an unremovable route that allows any subnet to route to any other subnet with the same VPC. The route maps the primary VPC address range to "local".
Subnet ID
Each subnet has a unique ID.
Subnet Types
Regardless of the type of subnet, the internal IPv4 address range of the subnet is always private, it is not routed.
Public Subnet
If a subnet's explicit or implicit route table contain a route, usually 0.0.0.0/0, to an internet gateway, the subnet is known as a public subnet. A subnet can auto-assign public IPv4 address. Does that make it a public subnet?
Private Subnet
If a subnet does not have a route in its explicitly associated route table or, if not implicitly associated, in the VPC main route table to an internet gateway, it is known as a private subnet. Usually the route to the gateway is 0.0.0.0/0. Subnets that have routes to NAT gateways are still considered private subnets. An instance in a private subnet is not publicly accessible even if it has an Elastic IP address or a public IP address associated with it, because the IP address is not routed to the subnet.
VPN-Only Subnet
If a subnet does not have a route to an internet gateway, but has its traffic routed to a virtual private gateway for a site-to-site VPN connection, it is known as a VPN-only subnet.
Subnet Security
AWS provides two features that can be used to secure the VPC:
Security Groups
Security groups control inbound and outbound traffic for instances.
Network ACLs
Network ACLs control inbound and outbound traffic for subnets. Each subnet must be associated with a network ACL.
Mapping Public IP Addressed on Launch
A subnet can be configured so instances that are launched in this subnet receive a public IP address. By default, the behavior is turned off.
Subnet Operations
Route Table
A route table is a set of rules, called routes, that are used to determine where network traffic is directed. Each route specifies a destination CIDR and a target - the most specific routes that match are used to determine how to route the traffic. This is called "the longest prefix match" rule. Every route table contains a local route for communication within the VPC over IPv4. If the VPC has more than one IPv4 CIDR block, the route tables contain a local route for each IPv4 CIDR block.
A subnet must be associated with one and only one route table, but one route table can be associated with multiple subnets. If no route table is explicitly associated with the subnet, the subnet is implicitly associated with the VPC main route table. It is said to be implicitly associated because the VPC main route table does not list the subnet amongst those subnets it was explicitly associated with. It does show it in a separated list, with the following caption "the following subnets have not been explicitly associated with any route tables and are therefore associated with the main route table".
The subnet's route table, whichever it is, controls routing for the subnet.
Any route table comes with the a rule similar to:
10.7.0.0/16 -> local
The rule lists the primary IP address range of the VPC, as a CIDR block, with a "local" target. This rule cannot be deleted. This rule means that any subnet will be routed by default to any subnet within the VPC.
CIDR blocks for IPv4 and IPv6 are treated separately. For example, a route with a destination CIDR of 0.0.0.0/0 (all IPv4 addresses) does not automatically include all IPv6 addresses. You must create a route with a destination CIDR of ::/0 for all IPv6 addresses.
VPC Main Route Table
The VPC main route table is the default route table for the VPC - all VPC subnets are implicitly associated with it, unless they are explicitly associated with other route tables. The routes in the main route table can be modified. One way to protect a VPC is to leave the main route table in its original default state, with only the local route, and explicitly associate each new subnet with custom route tables. This gives control over how each subnet routes outbound traffic.
Main Router
The VPC has an implicit, main router configured based on the VPC main route table
Gateways
When an Internet gateway, an egress-only Internet gateway, a virtual private gateway, a NAT device, a peering connection, or a VPC endpoint is added in the VPC, the route table for any subnet that uses these gateways or connections must be updated.
Internet Gateway
An internet gateway enables communication over the internet. An internet gateway is attached to the VPC.
To give a subnet access to internet, add a route with a destination of 0.0.0.0/0 for IPv4 traffic or ::/0 for IPv6 traffic, and a target of the Internet gateway ID (igw-xxxxxxxx).
VPC-Gateway Attachment
An internet gateway is not attached with any VPC after creation, an AWS::EC2::VPCGatewayAttachment resource must be created to attach the internet gateway to a VPC.
Internet Gateway Operations
NAT Gateway
NAT Gateways provide external access for private subnets. For example, if ECS tasks are running in private subnets, external access needs to be added so the task can pull the associated container images from their corresponding ECR repositories. One way to enable external access, without allowing unsolicited inbound connections is to create and use a NAT gateway. To enable instances in a private subnet to connect to the Internet, you can create a NAT gateway or launch a NAT instance in a public subnet, and then add to the route table associated with the private subnet a route that routes IPv4 Internet traffic (0.0.0.0/0) to the NAT device.
Elastic IP
A NAT gateway must be associated an elastic IP address, which is routable on the Internet. Even if the NAT gateway gets its elastic IP address, it still needs to be deployed behind an internet gateway so that public IP address is routed. That means the NAT must be deployed in a public subnet, has the routing configured to route the elastic IP of the NAT gateway externally to the internet. The private subnets that want unidirectional outbound internet connectivity will route to the NAT gateway. The NAT gateway is reachable over its private IP address, which is routed - and reachable - inside the VPC.
The NAT is associated with the elastic IP in CloudFormation using the "AllocationId" attribute, as follows:
Resources:
NATGateway:
Type: AWS::EC2::NatGateway
Properties:
...
AllocationId: !Ref ElasticIP
NAT Gateway Operations
Egress Only Internet Gateway
The IPv6 equivalent of NAT gateway.
Virtual Private Gateway
Virtual Private Network (VPN) Connection
A VPN connection enables communication between cooperating networks, such as a VPC and a corporate network.
Security
Security Group
- Amazon EC2 Security Groups for Linux Instances https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html
A security group acts as a virtual firewall for instances. The security group controls inbound and outbound traffic. You can specify one or more security groups when you launch an instance. A security group contains a set of rules that control the inbound traffic and a different set of rules that control the outbound traffic. All other traffic is discarded.
The rules can be modify at any time; the new rules are automatically enforced - it is sufficient to add a new rule with the CLI or via the management interface and the rule takes effect immediately, without requiring instance reboots.
There is an upper limit for both inbound rules (60) and outbound rules per security group. The limit can be changed through the Service Quotas service by navigating to Service Quotas → AWS services → Amazon Virtual Private Cloud (Amazon VPC) → Inbound or outbound rules per security group.
Security Group ID
Security Group Operations
Network Access Control List (ACL)
VPC and DNS
Instances executing in a default VPC are provided with a public and private DNS name, which correspond to the private and public IPv4 addresses of the instance.
Instances executing in a non-default VPC are provided with private DNS names, which correspond to the private IPv4 address of the instance. The instances may be provided with public DNS names, which correspond to the public IPv4 of the instance, if the following configuration attributes are set to true:
enableDnsHostnames
If set to true, the instances launched in this VPC get public DNS names (but only if enableDnsSupport is set to true.
enableDnsSupport
If set to true, the VPC supports DNS resolution.
Private Hosted Zones for VPC
To use private hosted zones, set enableDnsHostnames and enableDnsSupport to true when creating the VPC. Also see:
VPC Quotas and Limits
PrivateLink
AWS PrivateLink provides secure, private connectivity between Amazon VPCs, AWS services, and on-premises applications, using the the private AWS network.
VPC Endpoints
A VPC endpoint enables customers to privately connect to supported AWS services and VPC endpoint services relying on AWS PrivateLink. Amazon VPC instances do not require public IP addresses to communicate with resources of the service. Traffic between an Amazon VPC and a service does not leave the Amazon network.